SAP provides a standard Security Audit log functionality via transaction SM19 to record security-related system information such as changes to user master records or unsuccessful login attempts. By activating the audit log, you keep a record of those activities which can be accessed using transaction SM20 transactions.
Go to transaction SM19 or RSAU_CONFIG (for SAP Netweaver 750 or higher), and there we have 2 options “Static configuration” and “Dynamic Configuration”. For RSAU_CONFIG, first, check and implement note 2743809.
Any changes done in “Static configuration” will only be activated after you restart SAP. So if you want to activate the logging without restarting the system, then “Dynamic configuration” can help you in that case.
For both the configuration you can set multiple filters for different clients and users and with different logging settings.
Click on the “Create” icon to create a new audit profile. Enter a profile name and click continue.
Now maintain the configuration as per your requirement and click on “Filter active”. Once done, click on the “Activate” icon to activate the audit configuration.
Note: In the case of “Static Configuration”, this profile will only become active after you restart your SAP system.

How to activate the Dynamic SAP security audit log?
In SM19, there is a second tab as “DynamicConfiguration”. Just click on it and there we have similar filter options which we can activate.
Activate the filter and then click on the “Activate” icon. SAP will start logging in immediately.
Note: Dynamic configuration will deactivate after system restart. So make sure you have static configuration activated as a long-term solution.

What are the required Audit profile parameters?
The audit files are located on the individual application servers. You specify the location of the files and their maximum size in the following profile parameters:
rsau/enable = 1 (to Enable Security Audit)
rsau/selection_slots = 10 or more depending on how many filters you want to set.
rsau/user_selection = 1 (Defines the user selection method used inside kernel functions)
rsau/integrity = 1 (This helps to avoid data loss)
If you have kernel profile parameters FN_AUDIT (Name of security audit file) and DIR_AUDIT (Directory for security audit files) maintained, then make sure they don’t have the same values. Because if both point to the same path, then in that case there could be a loss of data as explained in note 2033317.
How to check the SAP security audit log?
Use transaction SM20 or execute report RSAU_SELECT_EVENTS to check the audit logs. Provide the selection criteria in the filters to narrow down the logs and then click on “Reread Audit Log”.
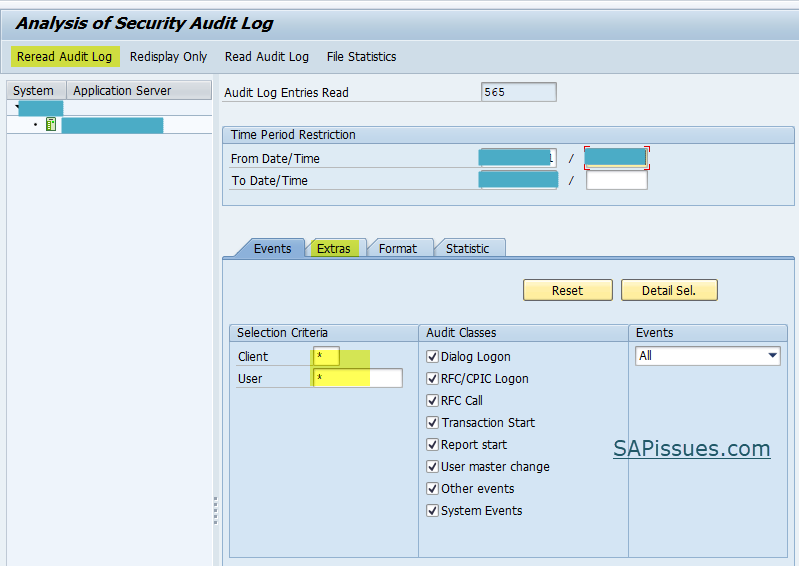
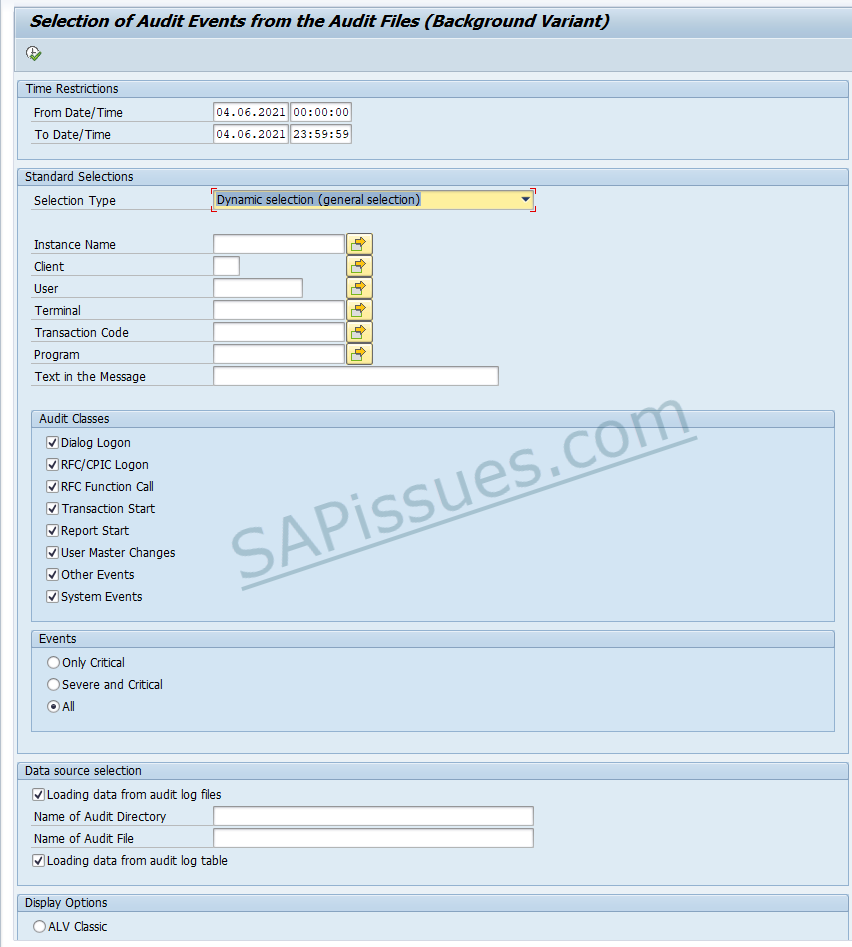
In the case of RSAU_READ_LOG ( For SAP Netweaver 750 or higher), we get similar options for selection and output layout as shown below:
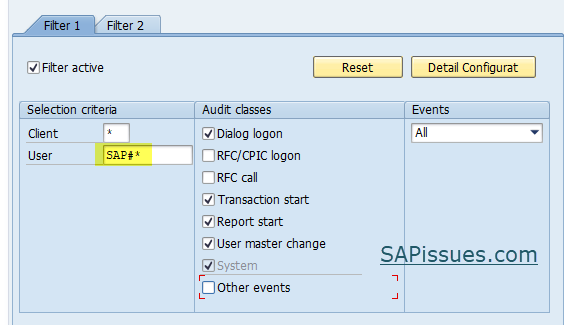
How to activate logging for SAP* user specifically?
In the user filter, we cannot provide SAP* as this will specify that we want SAP to start logging data for all the users starting with SAP and * as a wildcard. This will create unnecessary logging for user like SAPSYS which performs a lot of housekeeping activities which is not required to be logged.
So in that case, we have to provide the user as SAP#*
Is it possible to activate logging on “User group” ?
Yes, its possible to activate audit logging on “User group”. If you don’t this option, then you need to update your kernel to the version mentioned in note 2090487 and then implement correction instructions as per note 2285879.
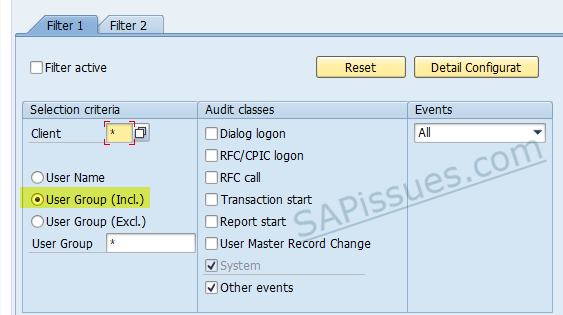
Is there a standard audit logging configuration provided by SAP?
Yes, SAP has provided a standard filter configuration file in sap note 2676384, which you can upload to your system using report RSAU_TRANSFER or create a profile manually using SM19 using the below filters:
- All clients (“*”), user “SAP#*”: Record all events. The character # serves to mask * as a non-wildcard.
- All clients (“*”), user “<your emergency user IDs>*”: Record all events.
- Client 066, all users (“*”): Record all events. (Client 066 is not used anymore by SAP. So you may delete it)
- All clients (“*”), all users (“*”): Record all events except AUW, AU5, AUK, CUV, DUR, and EUE (deactivate via “Detailed Display”).
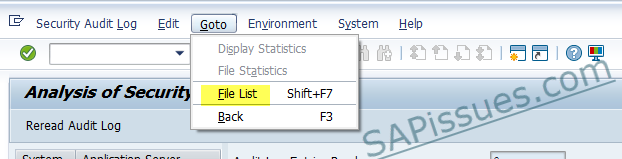
How to check if audit files are getting created?
Go to transaction SM20 –> Goto –> File list. This will provide all the audit files created till now on the server.
Is it possible to archive SAP security audit log files?
On SAP Netweaver 740 and below, SAP does not provide an archive connection for audit files. However, you can copy the audit files (that are already closed) to another medium and evaluate these files using the report RSAU_SELECT_EVENTS if required.
We recommend that you store the files of each application instance in a separate directory on the target medium (to avoid possible file name conflicts).
For SAP Netweaver 750 and above, we first need to configure to create audit files on the database and File System.
Go to RSAU_CONFIG –> Parameters and click on Edit.
Change the option for “Recording Target” to “Record in Database and File System” or “Record in Database”. Also, choose the “Recording Type” to “Audit Log with Archive Interface”. Table RSAU_BUF_DATA stores the audit logs on the Database level.

You can use transaction RSAU_ADMIN or direct access via transaction SARA to create an archive for the archiving object BC_SAL or run report RSAU_ARCHIVE_WRITE.
How to transfer SAP security audit log data from file system to database?
SAP provides a standard report RSAU_LOAD_FILES to transfer the audit log files created earlier on the file system to the database. Make sure you have note 3055825 installed to enable this functionality.
